2078 (2021)
Computer Science
Time: 3 hrs.
Full Marks: 75
Group 'A'
(Long answer questions)
Attempt any four questions.
1.a. Explain any three different types of operators in C with example.5
b Write a program to print fibonacci series 6,12,18,30 ... upto 10 terms using loop.
2. a) What is pointer ? Write the advantages of pointer.
b) What is string function ? Write a program to concatenate two string.2+3
3.
a)Write a program to calculate the factorial of any positive number. S
b)Write the importance of OOPs.
4. Define normalization. Explain 2NF and 3NF with example.
5 Write a program to input emp_no, name and salary of 100 employees using
structure. Display the name and salary of employee using structure. 10
Group 'B' 7x5=35
(Short answer questions)
Attempt any seven questions.
6.What is feasibility study ? Explain.[5]
7 Describe the desirable characteristics of a system analyst.[5]
8.Explain the different database model with suitable examples.[5]
9.Explain entity, attribute and relationship in Relational Database Management
System.[5]
10. Explain the role of Database administrator (DBA).[5]
11. Explain about coaxial cable and fiber optics cable.5
12. Define the term "constant", "identifier" and "keyword" in C program. 5
13. How can you minimize computer crime ? Explain.
14.What is E-Commerce ? List out demerit of E-Commerce.
15.Write short notes on:
a) Polymorphism.
b) Use of AI
-------------------------------------------------------------------------------------------------------------------
Solutions:
1.
a. Explain any three different types of operators in C with example.5
1)Arithmetic operator: It is used to do arithmetic calculations/operation.
It has following types.
+ -----------> used for addition.example is a+b. It means we are performing addition with the help of operand a and b
- ------------>It is used for subtraction.Example is a-b. It means we are performing subtraction with the help of operand a and b
* -------------------->used for multiplication.example is a*b. It means we are performing multiplication with the help of operand a and b
/---------------->used for division.example is a/b. It means we are performing division with the help of operand a and b
example
int a=5;
if(!(a==5))
{
printf("it is\n");
}
else
{
printf("it is not\n");
}
here ,the value is 5 but we get output "it is not".It is called reversing the output.
2. a) What is pointer ? Write the advantages of pointer.
Ans:-
Pointer:-
A pointer is a variable that stores a memory address. Pointers are used to store the addresses of other variables or memory items. Pointers are very useful for another type of parameter passing, usually referred to as Pass By Address. Pointers are essential for dynamic memory allocation.
some advantages:
1.It handles memory effectively.
2.Useful in file handling
3.Reduces spaces.
4.Reduces execution time.
5.Pointers are used with data structures.
b) What is string function ? Write a program to concatenate two string.2+3
Ans:-
String function:This is a library function existing in string.h header file. some popular functions are strcpy(),strcmp(),strcat() etc. These all are used to simplify string related programs.Typical functions include the ability to handle arrays of strings, to left and right align and center strings and to search for an occurrence of text within a string.
second part:-
#include <stdio.h>
#include<string.h>
int main()
{
char str1[100],str2[100];
printf("Enter two strings = ");
scanf("%s%s",str1,str2);
strcat(str1,str2);
printf("After copying the string is %s ", str1);
return 0;
}
3.
a)Write a program to calculate the factorial of any positive number.
Ans:-
//program to find factorial value of a positive number
#include <stdio.h>
int main()
{
int n,factorial=1,i;
printf("enter a number\n");
scanf("%d",&n);
if(n<=0)
{
printf("%d is a negative number, so it can not be calculated",n);
}
else
{
for(i=1;i<=n;i++)
{
factorial=factorial*i;
}
printf("the factorial value=%d",factorial);
}
return 0;
}
b)Write the importance of OOPs.
Ans:-
- Modularity for easier troubleshooting. Something has gone wrong, and you have no idea where to look. ...
- Reuse of code through inheritance. ...
- Flexibility through polymorphism. ...
- Effective problem solving.
- message passing
- data hiding
- easy to maintain and upgrade
4. Define normalization. Explain 2NF and 3NF with example.
Ans:-
In the field of relational database design, normalization is a systematic way of ensuring that a database structure is suitable for general-purpose querying and free of certain undesirable characteristics—insertion, update, and deletion anomalies that could lead to a loss of integrity.
2N:
A table is said to be in 2 N if it is in 1N and there is no redundant data in table i.e. if a value of column is dependent on one column(primary key only) but not another.
For example:
Create table employee
(
Emp_no integer not null,
L-name varchar(20) not null,
F_name varchar(20),
Dept_code integer,
Description varchar(50),
);
This table contains redundant data i.e. the value of column(field) “description” depends on dept_code but does not depend on primary key “emp_no”.So let’s make a new table and shift them into that.
Create table employee
(
Emp_no integer not null,
L_name varchar(20) not null,
F_name varchar(20),
Dept_code integer,
);
Create table department
(
Dept_code integer not null,
Description varchar(50) not null,
);
We got two tables named employee and department with fields. Both the tables are related by primary key called dept_code. Now there is no redundancy and table is in 2N.
An entity is said to be in the third normal form when,
1) It satisfies the criteria to be in the second normal form.
2) There exists no transitive functional dependency. (Transitive functional dependency can be best explained with the relationship link between three tables. If table A is functionally dependent on B, and B is functionally dependent on C then C is transitively dependent on A and B).
Example:
Consider a table that shows the database of a bookstore. The table consists of details on Book id, Genre id, Book Genre and Price. The database is maintained to keep a record of all the books that are available or will be available in the bookstore. The table of data is given below.
Book id | Genre id | Book genre | price |
121 | 2 | fiction | 150 |
233 | 3 | travel | 100 |
432 | 4 | sports | 120 |
123 | 2 | fiction | 185 |
424 | 3 | travel | 140 |
The data in the table provides us with an idea of the books offered in the store. Also, we can deduce that BOOK id determines the GENRE id and the GENRE id determines the BOOK GENRE. Hence we can see that a transitive functional dependency has developed which makes certain that the table does not satisfy the third normal form.
Book id | Genre id | price |
121 | 2 | 150 |
233 | 3 | 100 |
432 | 4 | 120 |
123 | 2 | 185 |
424 | 3 | 140 |
table book
Genre id | Book genre |
2 | fiction |
3 | travel |
4 | sports |
table genre
After splitting the tables and regrouping the redundant content, we obtain two tables where all non-key attributes are fully functional dependent only on the primary key.
When all the column in a table describe and depend upon the primary key,the table is 3N.
5 Write a program to input emp_no, name and salary of 100 employees using
structure. Display the name and salary of employee using structure. 10
Ans:-
/*program to input emp_no, name and salary of 100 employees using structure.
Display the name and salary of employee using structure.
*/
#include <stdio.h>
struct employee
{
int emp_no;
char emp_name[100];
float emp_salary;
};
int main()
{
struct employee v[100];
int i;
for(i=0;i<=99;i++)
{
printf("enter employee id\n");
scanf("%d",&v[i].emp_no);
printf("enter employee name\n");
scanf("%s",v[i].emp_name);
printf("enter employee salary\n");
scanf("%f",&v[i].emp_salary);
}
printf("records are\n");
for(i=0;i<=99;i++)
{
printf("employee id=%d,employee name=%s and employee salary=%f\n",v[i].emp_no,v[i].emp_name,v[i].emp_salary);
}
return 0;
}
Group 'B' 7x5=35
(Short answer questions)
Attempt any seven questions.
6.What is feasibility study ? Explain.[5]
Ans:-
It has following types.
7 Describe the desirable characteristics of a system analyst.[5]
Ans:-
System analyst:-
The persons who perform above task/system analysis,design and implementation activity is know as system analyst. Somewhere we say or call by names like business engineer, business analyst etc. The work of system analyst who designs an information system is just same as an architect of a house. They work as facilitators of the development of information systems and computer applications.
characteristics:-
- verbal communication
- non-verbal communication
- listening skills
- problem solving
- decision making
- assertiveness (Communicating our values, ideas, beliefs, opinions, needs and wants freely.
8.Explain the different database model with suitable examples.[5]
Ans:-
Hierarchical model:-
Hierarchical database is a model in which data is organized into a tree-like structure. In this,
Data is organized like a family tree or organization chart
The parent record can have multiple child records – child records can only have one parent
Pointers link each parent record with each child record
Complex and difficult to maintain
This structure allows one 1:N relationship between two types of data. This structure is very efficient to describe many relationships in the real world; recipes, table of contents, ordering of paragraphs/verses,
Example:
We can see here a parent node with many branches called children.Each child has their own record with furhher informations.In given diagram, the first record has name “Ram” with street “Baneshwor” and city named kathmandu. It is further linked to its balance id and amount. In same fashion all others records have, they all are related or linked to their id and amount. We can see records’ arrangement in tree like format.
Advantages:- 1) easiest model of database.
2) Searching is fast if parent is known.
3) supports one to many relationship.
Disadvantages: 1) old and outdated one.
2) Can not handle many to many relationships.
3) More redundancy.
Relational model: - Three key terms are used extensively in relational database models: relations, attributes, and domains. A relation is a table with columns and rows. The named columns of the relation are called attributes, and the domain is the set of values the attributes are allowed to take.
The basic data structure of the relational model is the table, where information about a particular entity is represented in columns and rows. Thus, the "relation" in "relational database" refers to the various tables in the database; a relation is a set of tuples.So,
Relational databases
Data is organized into two-dimensional tables, or relations
Each row is a tuple (record) and each column is an attribute (field)
A common field appears in more than one table and is used to establish relationships
Because of its power and flexibility, the relational database model is the predominant design approach
In this table we have used different concept like field (each column),record (each row). Each row gives us a complete information. If we have many tables then we relate them for data extractions, this is called relationship between tables.Apart from these, we also use other concept like, primary key, foreign key, Entity etc.
9.Explain entity, attribute and relationship in Relational Database Management
System.[5]
Ans:-
The Entity-Relationship (E-R) data model is based on a perception of a real world that consists of a collection of basic objects, called entities, and of relationships among these objects. An entity is a “thing” or “object” in the real world that is distinguishable from other objects. For example, each person is an entity, and bank accounts can be considered as entities.
Entities are described in a database by a set of attributes. For example, the attributes account-number and balance may describe one particular account in a bank, and they form attributes of the account entity set. Similarly, attributes customer-name, customer-street address and customer-city may describe a customer entity.
A relationship is an association among several entities. For example, a depositor relationship associates a customer with each account that she has. The set of all entities of the same type and the set of all relationships of the same type are termed an entity set and relationship set, respectively.
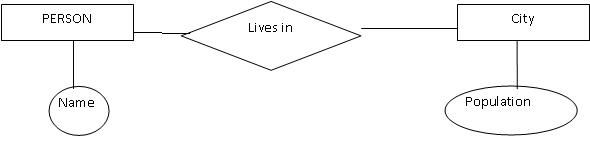
The overall logical structure (schema) of a database can be expressed graphically by an E-R diagram, which is built up from the following components:
Entity:-It represents tables with fields and records. For this we use rectangular shape.
Attributes:- These are the properties of an entity associated with. We can find this in column. We use Elliptical shape to represent attributes.
Relationship:- When we connect many tables, it is called relationship. For this we use Diamonds.
Example:
10. Explain the role of Database administrator (DBA).[5]
Ans:-
A database administrator (DBA) is a person/s who is/are responsible for the environmental aspects/activities related to database. The role of a database administrator has changed according to the technology of database management systems (DBMSs) as well as the needs of the owners of the databases.
Duties/roles:
1. Installation of new software.
2. Configuration of hardware and software with the system administrator
3. Security administration
4. Data analysis
5. Database design (preliminary
6. Data modeling and optimization
7. Responsible for the administration of existing enterprise databases and the analysis, design, and creation of new databases
11. Explain about coaxial cable and fiber optics cable.5
Ans:-
12. Define the term "constant", "identifier" and "keyword" in C program. 5
Ans:-
constant:- In our program, if a value of a variable does not change, it is called constant.
Example:
int a=78;
Here, a is a variable and has value 78. It(78) is called constant.
Similarly, we may use some keywords const or define for cosntant value.
Keyword:- It is a reserved word or pre-defined word existing in a library of compiler. We can not edit or change it. Example: int,float,char,for etc
We can not use this as variable in our program.
Example:
int a=90;
int is a keyword.
Identifier: This is a name we give to our variables or constants in our program. Using this name we store our value in the memory of computer.
Example:
int a;
Here, 'a' is an identifier.
We can not start name with digit or we can not put space in the name.
13. How can you minimize computer crime ? Explain.
Ans:-
Alternatively referred to as cyber crime, e-crime, electronic crime, or hi-tech crime. Computer crime is an act performed by a knowledgeable computer user, sometimes referred to as a hacker that illegally browses or steals a company's or individual's private information. In some cases, this person or group of individuals may be malicious and destroy or otherwise corrupt the computer or data files.
Below is a listing of the different types of computer crimes today. Clicking on any of the links below gives further information about each crime.
Child pornography - Making or distributing child pornography.
Cyber terrorism - Hacking, threats, and blackmailing towards a business or person.
Cyberbully or Cyberstalking - Harassing others online.
Creating Malware - Writing, creating, or distributing malware (e.g. viruses and spyware.)
Denial of Service attack - Overloading a system with so many requests it cannot serve normal requests.
Espionage - Spying on a person or business
To minimize we may apply following methods.
1. Use a full-service internet security suite
2. Use strong passwords
3. Keep your software updated
4. Manage your social media settings
5.Talk to your children about the internet
6. Keep up to date on major security breaches
14.What is E-Commerce ? List out demerit of E-Commerce.
Ans:-
E-commerce:
E-commerce (electronic commerce) is the buying and selling of goods and services, or the transmitting of funds or data, over an electronic network, primarily the internet. These business transactions occur either as business-to-business (B2B), business-to-consumer (B2C), consumer-to-consumer or consumer-to-business.
The terms e-commerce and e-business are often used interchangeably. The term e-tail is also sometimes used in reference to the transactional processes that make up online retail shopping.
Merits:-
Following are some merits of E commerce.
- Faster buying process.
- Store and product listing creation.
- Cost reduction.
- Affordable advertising and marketing.
- Flexibility for customers.
- No reach limitations.
- Product and price comparison.
- Faster response to buyer/market demands.
15.Write short notes on:
a) Polymorphism.
Ans:-
b) Use of AI
Ans:-Following are some uses of AI.
- Personalized Shopping.
- AI-powered Assistants.
- Fraud Prevention.
- Administrative Tasks Automated to Aid Educators.
- Creating Smart Content.
- Voice Assistants.
- Personalized Learning.
- Autonomous Vehicles.